Agile Development
Harnessing the synergies between Agile Development, Secure, Coding, Continuous Integration and Continuous Delivery to build and enhance mission critical systems.

Cybersecurity
Delivering secure and resilient systems to protect critical information against modern-day attack vectors.

Cloud Services
Transforming systems into cloud-native applications to allow organizations to automatically scale infrastructure to match business needs.

Enterprise Content Management (ECM)
Providing secure document lifecycle management with enterprise-wide control over any type of content with comprehensive security and privacy.

Business Process Management (BPM)
Seamlessly integrating rules within business processes to standardize operational decisions and ensure consistent execution of business workflows.

Machine Learning
Implementing machine learning frameworks to intelligently automate complex business functions which traditionally required human intervention.
Platform Services
Delivering multi-tenant Platform as a Service (PaaS) offerings through virtualization and containerization.

Intelligent Capture
Digitizing paper records with optical character recognition (OCR) conversion and automating metadata capture.
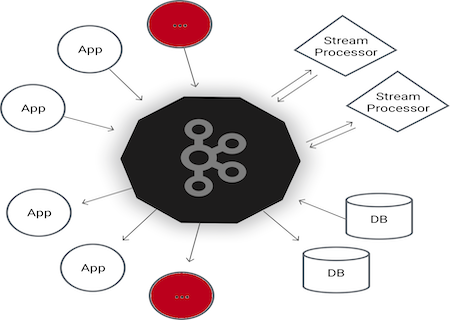
Enterprise Messaging
Provisioning an event-based messaging platform capable of distributing trillions of messages a day.